Ensuring Permission Integrity
Quality is paramount at Sycorr, and knowing that the permission information being imported into Permission Assist is an accurate reflection of the third-party application information is crucial. Due to the criticality of ensuring permission integrity, Sycorr dictates an above average approach in both the system and the process. Sycorr achieves a high level of quality based on a fixed process from conception to client release. This process contains milestones - each with their own requirements, expected outcomes, and artifacts. These milestones and the details of each are outlined below.
Milestone 1 - Discovery
In the majority of cases, the development of a new third-party application integration occurs when a bank decides to sponsor adding a new application permission importer to Permission Assist. When this occurs Sycorr and the sponsoring bank participate in a formal discovery process, during which the application owners provide detailed information about all facets of how permissions within the third-party application are reviewed and applied. Details such as options for reporting on such data are also shared and discussed, especially when more than one option is present or when reporting is extremely difficult.
Expected artifacts of this phase include sample files from the bank's system and application documentation.
Sycorr fully understands we are working with sensitive data. As a result, we request files are sent in a secure fashion. Upon receiving a secure set of files, the files are sanitized which means we remove the bank name and convert employee names and usernames to fake employees and usernames that are symmetric to our test environment (not applicable to non-modifiable documents such as PDF files). This process ensures that we're attempting to minimize your exposure from the first moment.
Due to unique client situations, not all clients are on the newest version of specific on-property systems. As a result, Sycorr may support multiple versions of the same application due to reporting changes.
Milestone 2 - Development
After the artifacts from the Discovery phase are sanitized, they are sent to the Software Development team for active development. Thus far, permissions have been imported in the following formats:
-
Text file (CSV, Pipe-delimited, Ragged, and Custom formats)
-
Excel Workbook (XLSX)
-
Excel 97-2003 Workbook (XLS)
-
Portable Document Format (PDF)
-
Direct API / Database Integration
In all the file format integrations, the Software Development team is required to use base libraries built, tested, and maintained by Sycorr to open, read, and parse these files. This ensures all developers are using a standard and proven method for reading the permission data from files.
During the development process, the first line of continuous testing is put into place - automated unit tests. It is the responsibility of the Software Developer to write tests that do continuous spot checking of the integrity of the results. For example, a Software Developer may write tests that assert:
-
There are 43 Loan Officers in this file.
-
John Smith has an admin role.
-
Becky Jane has a wire-entry level of $70,000
Through a process called Test Driven Development (TDD), automated assertions such as these are written along with the permission importer code. TDD helps the developer ensure that all the permission expectations are completed and correct because the continuous assertions are written prior to development.
Once the developer has all the automated unit tests (expectations) passing, the developer does a manual integration test to ensure final quality at this phase. The developer will take the importer and add it to Sycorr's internal test environment, running multiple test migrations through it to ensure that user and permission data pass visual spot checking.
Finally, the developer submits the importer code and tests to our secure source code control system. Upon every source code change all application importers are automatically rebuilt, tested, and versioned for continuous integrity and stability using a Continuous Integration server. There are currently 150+ continuous automated tests, running 650+ assertions.
Milestone 3 - Sponsor Sign-Off
Before moving into further phases for public release to all clients, Sycorr completes a pre-verification process with the sponsoring client(s). Feedback can often be gathered through remote working sessions; however, some situations may dictate installing the application importer to a client/shared Permission Assist instance. Client validation intends to ensure that all information comes through accurately and may include user counts, entitlements, roles, and translations. Any errors are addressed, and the validation process is repeated until no issues are discovered. We will never release an application importer with undocumented, known issues.
After the sponsor has signed off, an importer may be considered ready for release to the sponsoring client(s) but generally not publicly available to all clients.
Milestone 4 - Release Versioning
Although an application importer may be deployed on its own (without requiring an update of Permission Assist), we also want to ensure that all clients have the option of installing any/all of the newest, stable application importers with their Permission Assist installation. Therefore, when an application importer is considered stable and ready to be released to all clients, it is integrated with the Permission Assist installation. Upon every source code change both Permission Assist and all application importers are strictly versioned using a Continuous Integration server. The versioning pattern is an industry standard of [major.minor.build].
Milestone 5 - Quality Assurance
Prior to any Permission Assist release the newest, stable, integrated version of Permission Assist is promoted to our internal test environment for a standard process quality assurance. Quality assurance consists of manual and automated testing. There are currently over 250+ tests and 650+ assertions for the Permission Assist application. All manual test scripts and automated tests must pass before it can be considered stable and ready to release to all clients.
Milestone 6 - Inter-Application Validation
The users of Permission Assist have been (and always will be) better at detecting issues than any machine ever could; however, as your partner, we continue to strive and provide you the tools, visualizations, and features to detect anomalies when they occur.
Circumstances that cause permission anomalies include the following:
-
New version upgrades of the third-party application
-
Enhancements to application importers that include additional permissions
-
Previously unseen (but valid) permission values emitted
-
Permission/user discrepancies between SaaS and on-property installations of third-party applications
Permission Assist continues to add new user experiences around application permission monitoring and validation so that when these anomalies occur, Permission Assist can help you quickly identify these types of situations. Some of these features include the following:
Through these features combined with thoughtful user design, Permission Assist inherently promotes a process that allows for full visibility of all permissions - from past to present, from import to completed review. Supervisors, Application Managers, Provision Team Members, and Information Security Officers all have an opportunity to review permissions and ensure integrity every step of the way.
Application Permission Imports
Permission Assist streamlines the process of uploading the files needed to holistically report application permissions. In some cases, multiple files of different types are required, while in other cases multiple files of the same type are required. To provide clarity around which files and expected file formats are required, Permission Assist clearly describes each file and file format required for a particular application as shown in the following example:
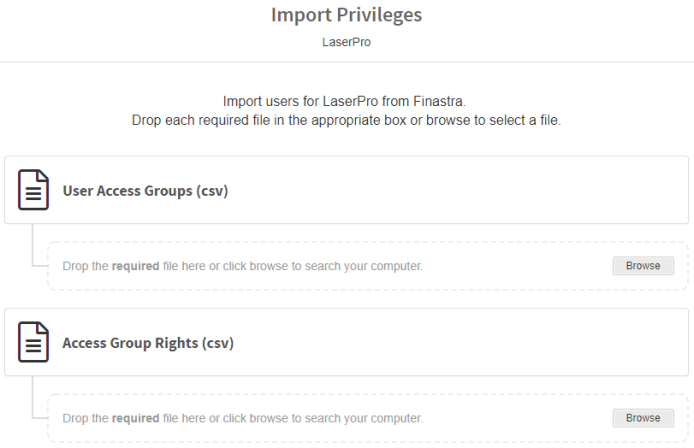
When a third-party application can leverage an API or scheduled imports to provide automatic importing, similar protections are taken to ensure the configuration is correct and the appropriate files are scheduled for import.
Application Import and Change Logs
Import Log and Import Summary
The Import Log within Permission Assist provides early progress and metrics through real-time display of progress as application permissions are being uploaded (see example below).
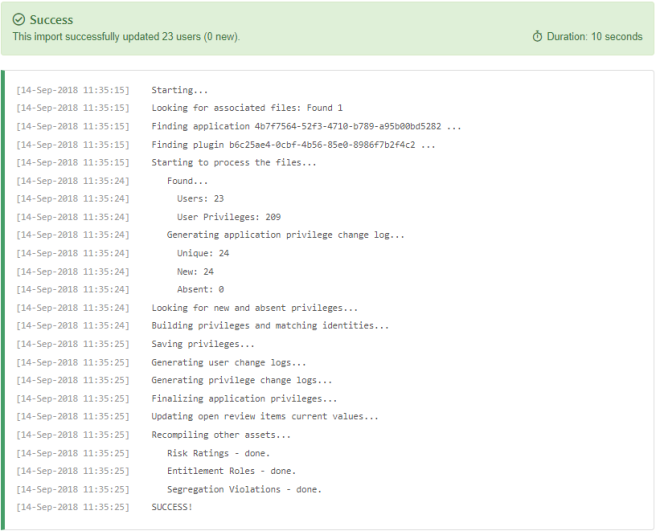
After the data is imported, a summary of new users and privileges is displayed (see example below).
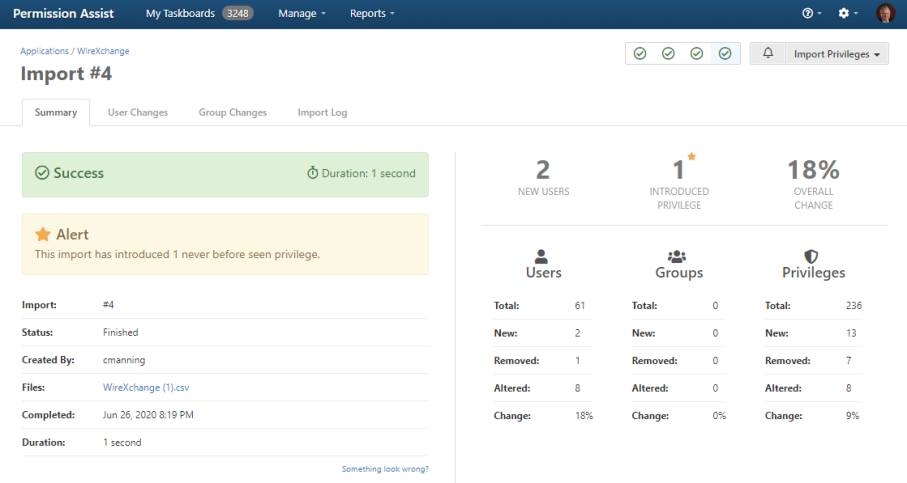
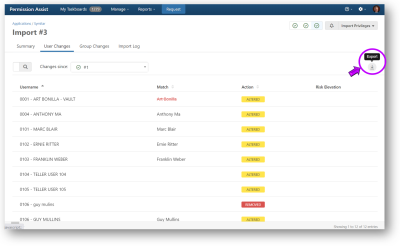
User Changes Log
The User Changes tab displays a list of all users that have been added or changed since the last import. If risk levels have been assigned to privileges within the application, Permission Assist is able to identify the potential risk those changes within the Risk Elevation column.
A more detailed view of the user's privileges as compared to a previous import is also available by selecting on a user within the list, and detailed reports of the changes.
Detailed reports of the changes are available in Excel or PDF format using the Export button (see below).
Sample Reports
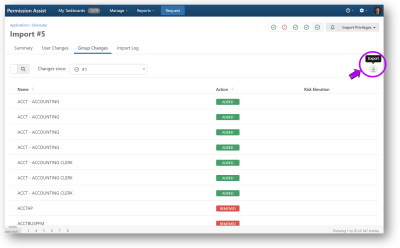
Group Changes Log
The User Changes tab displays a list of all groups that have been added or changed since the last import.
Detailed reports of the changes are available in Excel or PDF format using the Export button (see below).
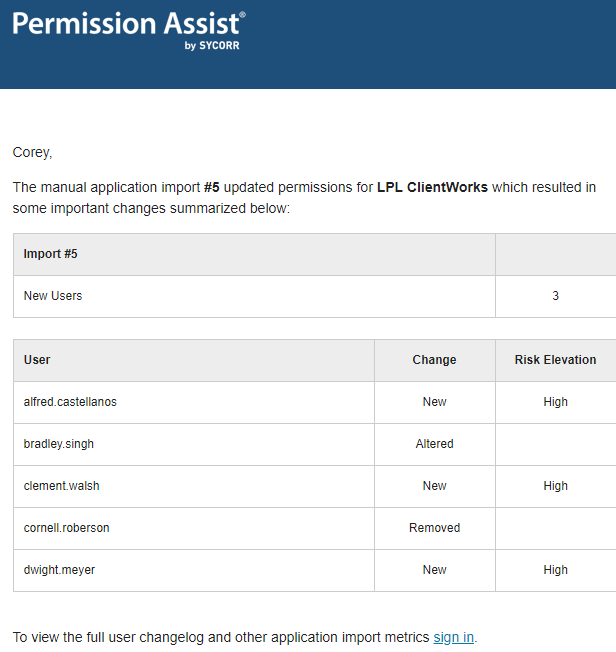
Application Alerts
Each user has the option of signing up for application alerts. When alerts are enabled for a specific application, Permission Assist sends an automatic email notification when user permissions for that application change. Within the email notification, a list of changes to permissions are highlighted along with the potential risk elevation associated with each change.
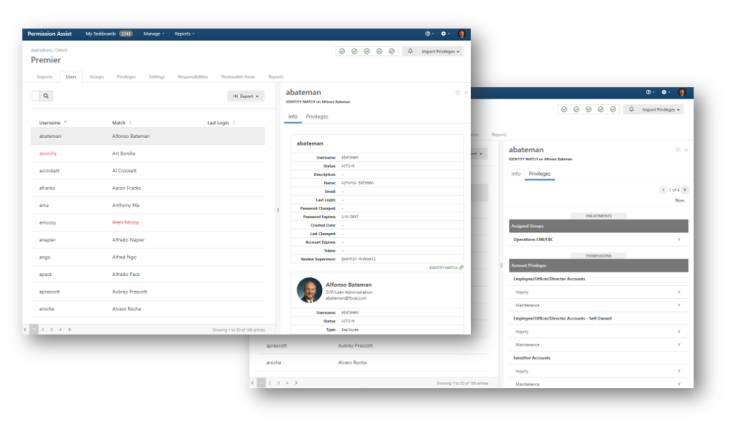
User and Group Privileges
The Users and Groups tabs on the application are the ultimate place for application managers to review their imported and formatted permission data prior to starting a review.
Within the Users area, you can view the user counts, browse through a list of users of the application, view a test identity match for each user, and drill down into the exact privilege data that will be leveraged during the next review.
Within the Groups area, you can view the group counts, browse through a list of users assigned to the group, and drill down into the exact privilege data that will be leveraged during the next review.
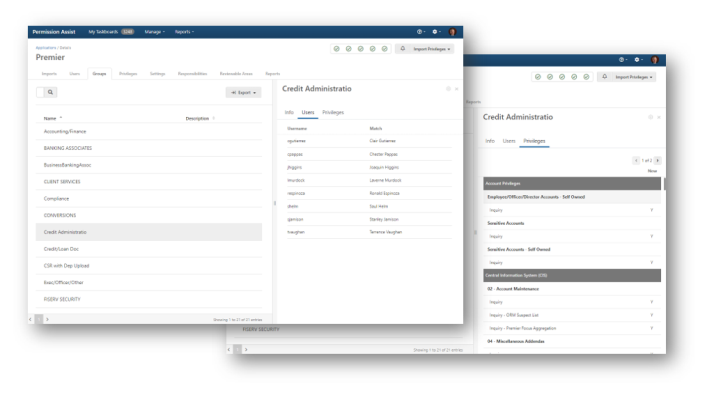
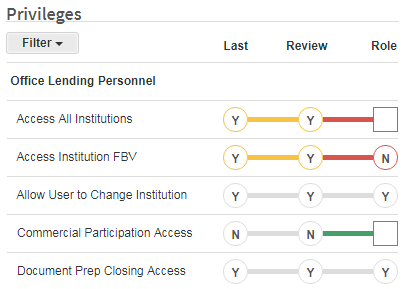
Then vs. Now - Permission Dumbbells
The "permission dumbbells" help streamline the review process by offering visual information of essential data so that permissions in the previous review can be compared to those in the current view. If the application also considers the role of each user, the Role column identifies whether the permission is set to the level or value expected for that role. When coupled with a multi-user review, the opportunity for many people of various levels to sign-off on permission integrity exists.
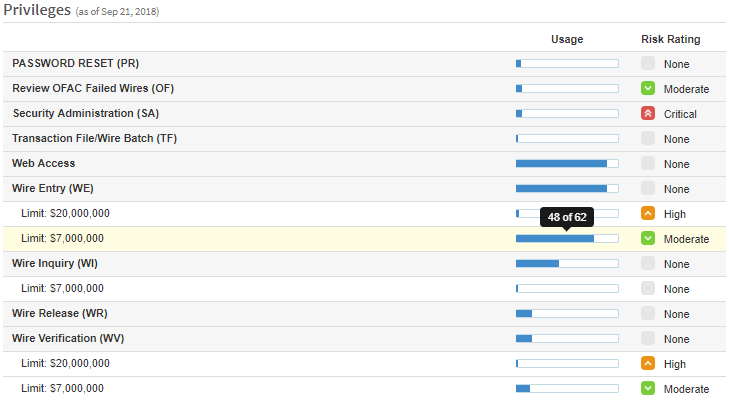
Permission Usage
Enhanced reporting allows you to visualize the usage (across all users) for all privileges within an application, which helps to identify overly loose provisioning.
Milestone 7 - Ongoing Support
From concept to support, Sycorr's dedication to quality software is unwavering. With you as our trusted partner, we build and maintain a quality standard not found among any other product vendors.
In the event you believe that an application permission importer is incorrect (whether you were the sponsor or not), our response to permission import problems is swift. You may contact us 24 hours a day using our support portal at: sycorr.com/support
We treat permission import issues as mission critical, thus our response time is, on average, within the same business day as initial contact. Average time to receive a patched permission importer is around 1 business day.